I’m pretty new to the F5 NLB scene, any network load balancing I had previously done had been through the inbuilt Windows Network Load balancing (WLB) Server role. Recently I was asked to deploy a F5 configuration to an already running production environment to handle SSL Termination, Caching and (of course) Load balancing on both web and app tiers.
The existing deployment comprised of two /22 segments (Internal and DMZ networks) with a single router as the default gateway; Everything I read online told me to use a “One armed F5 Config”. This type of config “should” let me add a single physical network to one of my segments and reach both networks using a SNAT rule to adjust the origin address on the reply; But how could this work if a router was translating requests between the two networks? I discovered after many hours, it can’t…
My answer, ensure the F5 is connected to both network segments and use Route Domains to solve my routing problems. Here’s what I did:
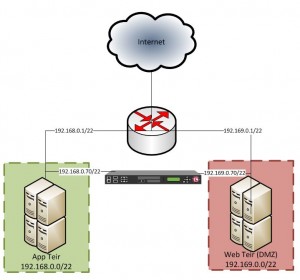
- Utilize a free port on my F5 to connect into both networks – Most people could probably just add another VLAN to their existing network, however I don’t have the ability to control the managed network
- Establish the 2nd untagged VLAN for the 2nd connection in Step 1
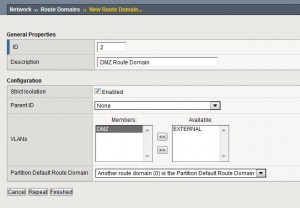
- Establish a new route domain from Network -> Route Domains -> Create.
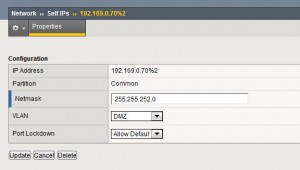
- Add a new Self-IP for the 2nd network connection on your new VLAN – Add %<routedomainID> after your IP
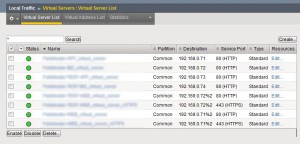
- Create a new Load balanced application/Virtual server and add %<routedomainID> to your VIP Address (NOTE: you will likely need to enable SNAT auto-map to the Virtual Server profile to allow return traffic via the Routedomain)
- You should “hopefully” be good to go – your application is now hopefully responding correctly and your health monitor is showing a friendly green status
This solution is merely a stop-gap until we can convert it into a routed configuration (recommended setup) – where the F5 unit will be the default gateway on both networks with something like a /29 stub network between the F5 and the router.
All in all, the F5 units are pretty blimmin powerful devices – I have a good handle on the UI but have only really scratched the surface using the BigPipe/TMSH commands. I KNOW that I’ve glossed over details, please feel free to leave a comment if you have any questions (it looks like there are many stuck Engineers on the net with the same problem)
-Patrick